Created: 26/07/2024 19:48
Last Updated: 13/08/2024 11:30
 Scenario:
Your digital forensics expertise is critical to determine whether data exfiltration has occurred from the customer’s environment. Initial findings include a compromised AWS credential, indicating a potential unauthorized access. This investigation follows from a customer report of leaked data allegedly for sale on the darknet market. By examining the compromised server and analyzing the provided AWS logs, it will not only validate the customer's breach report but also provide valuable insights into the attacker's tactics, enabling a more comprehensive response.
Scenario:
Your digital forensics expertise is critical to determine whether data exfiltration has occurred from the customer’s environment. Initial findings include a compromised AWS credential, indicating a potential unauthorized access. This investigation follows from a customer report of leaked data allegedly for sale on the darknet market. By examining the compromised server and analyzing the provided AWS logs, it will not only validate the customer's breach report but also provide valuable insights into the attacker's tactics, enabling a more comprehensive response.
Task 1: What type of scanning technique was used to discover the web path of the victim's web server? Specify the name of the corresponding MITRE sub-technique.
We got AWS Cloudtrail logs from several regions and artifacts gathered with UAC (Unix Artifact Collector), task mentioning web server so we could find access.log or error.log and start investigating from here
You can find both logs here after extracted them from tar.gz file
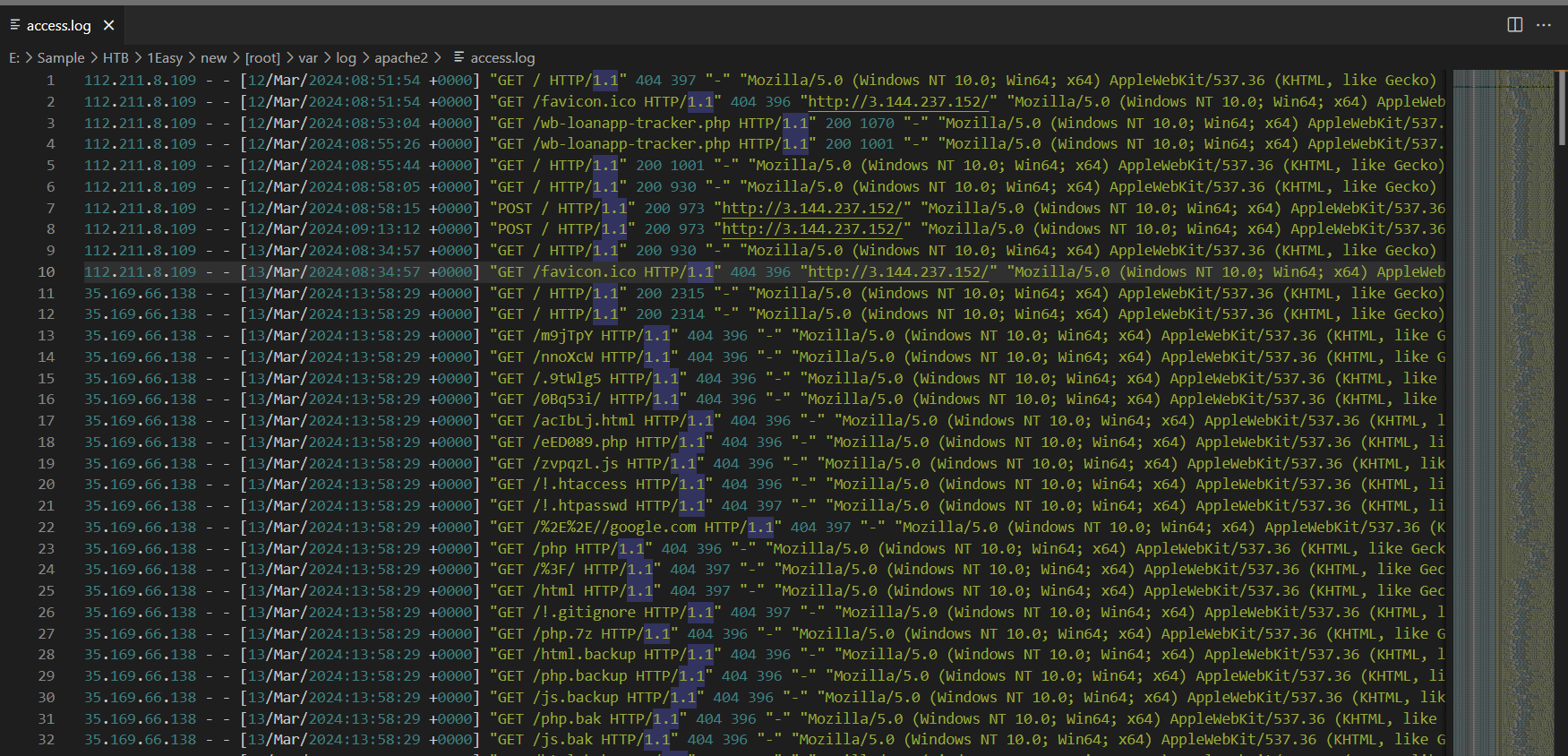
Then after examined access.log, we can see that there are several requests from 35.169.66.138 and we can clearly see that it is directory fuzzing or directory bruteforcing
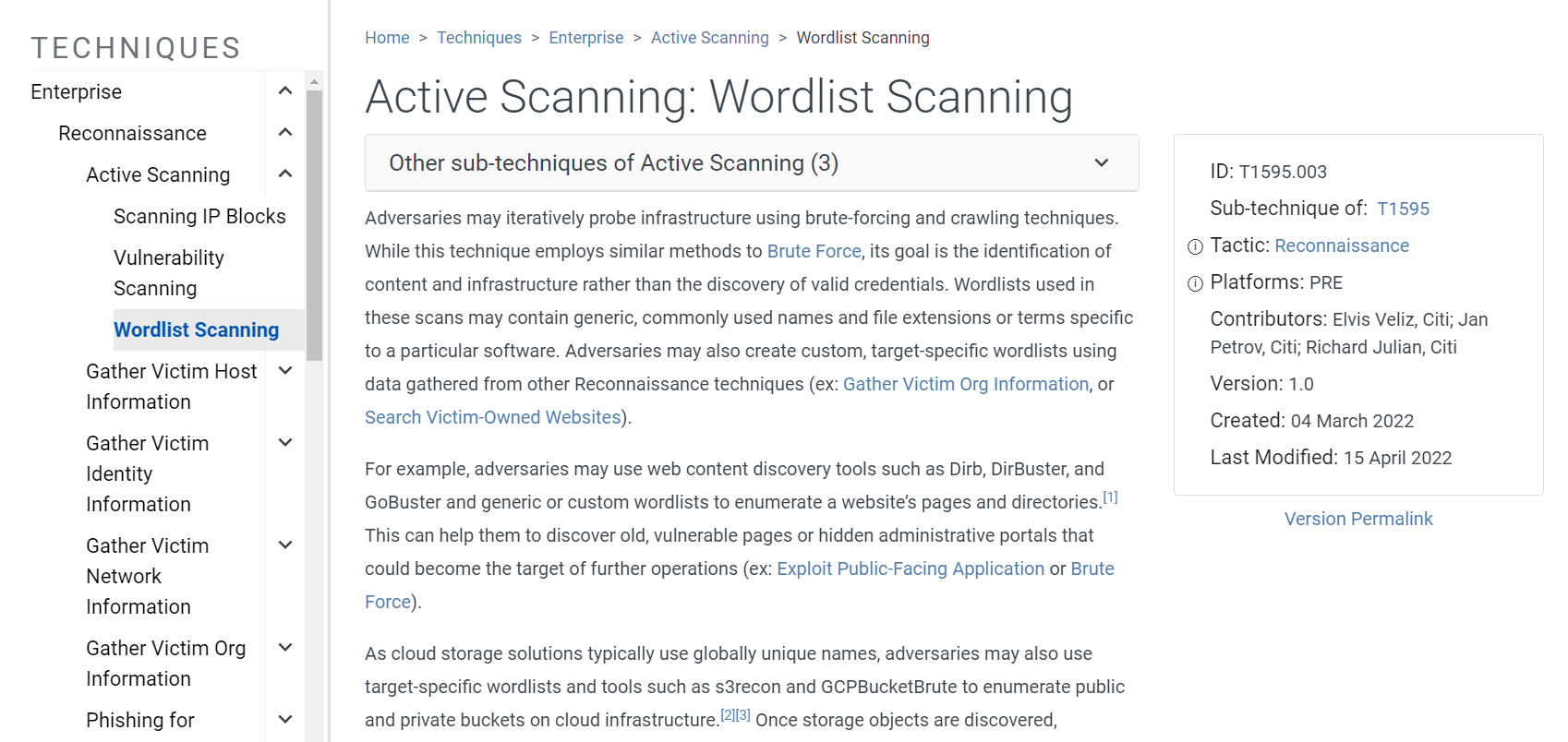
And according to MITRE ATT&CK, this action is called Wordlist Scanning
Wordlist Scanning
Task 2: It seems a web request possibly could have been rerouted, potentially revealing the web server's web path to the Threat Actor. What specific HTML status code might have provided this information?
There are 2 HTTP Status code that we might want to take a look which are
- 301 Moved Permanently: Permanent redirection.
- 302 Found: Temporary redirection.
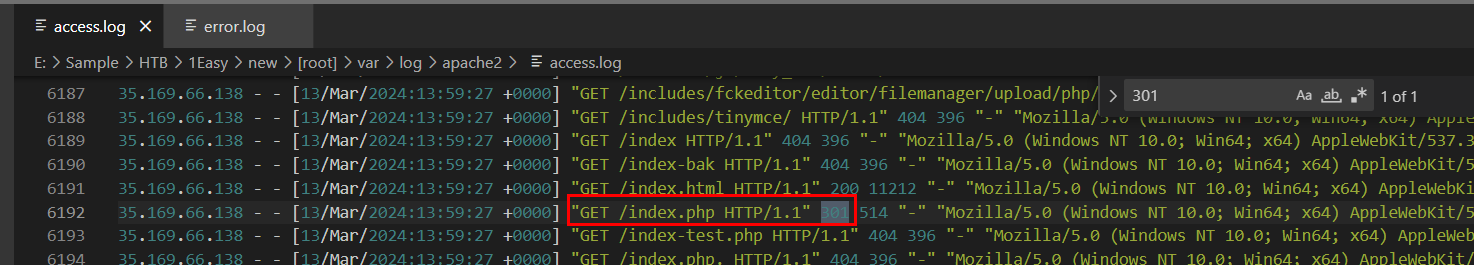
I didnot find 302 but I found one 301 so it has to be this one
301
Task 3: What was the initial payload submitted by the threat actor to exploit weakness of the web server?
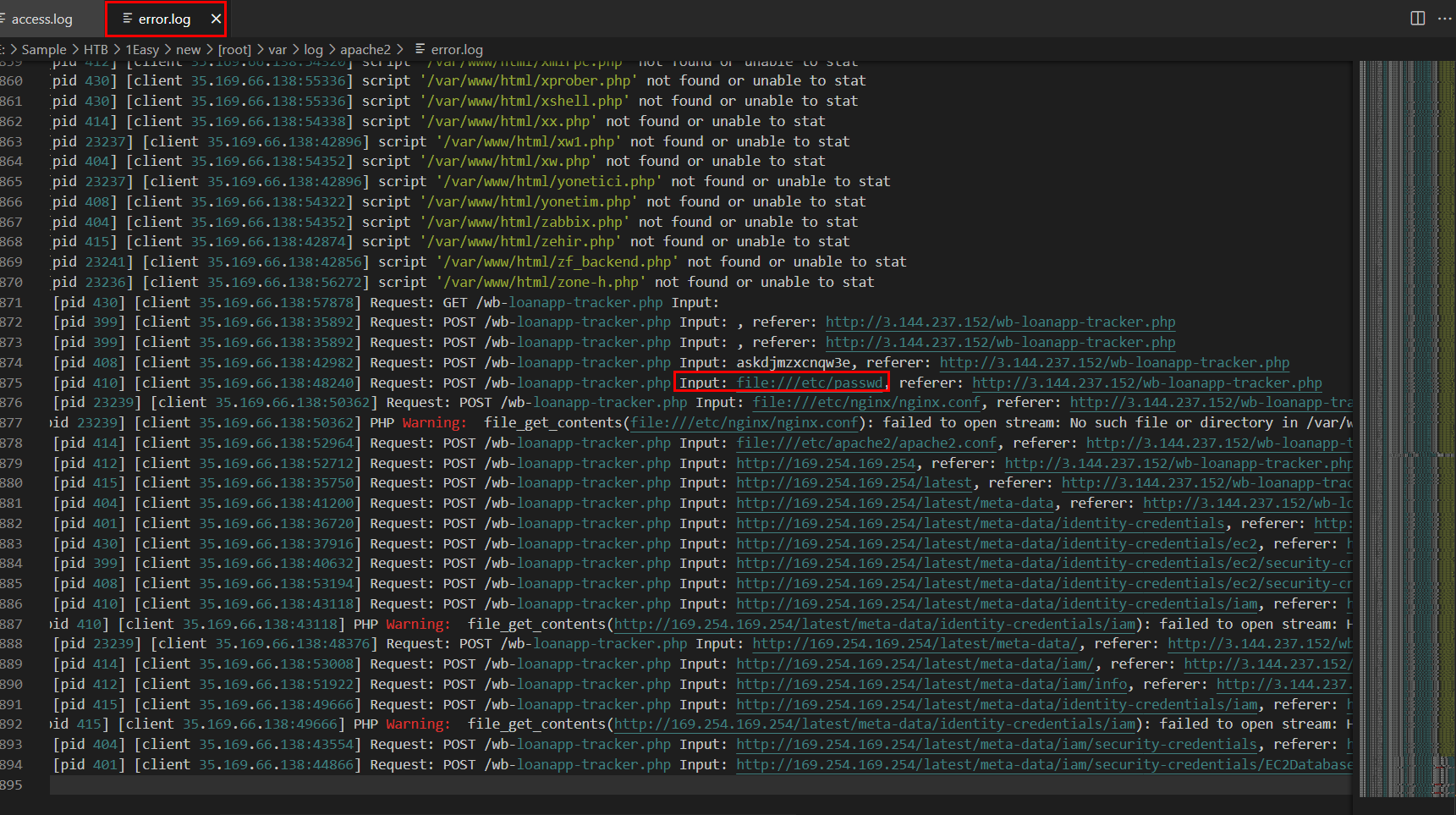
We have to investigate error.log and we can see that the threat actor tried to exploit LFI with file:///etc/passwd payload
file:///etc/passwd
Task 4: What is the name of the vulnerability exploited by the Threat Actor?
The Threat Actor send POST requests and get what he want from a server, it is SSRF
Server Side Request Forgery
Task 5: At what time (UTC) did the Threat Actor first realize they could access the cloud metadata of the web server instance?
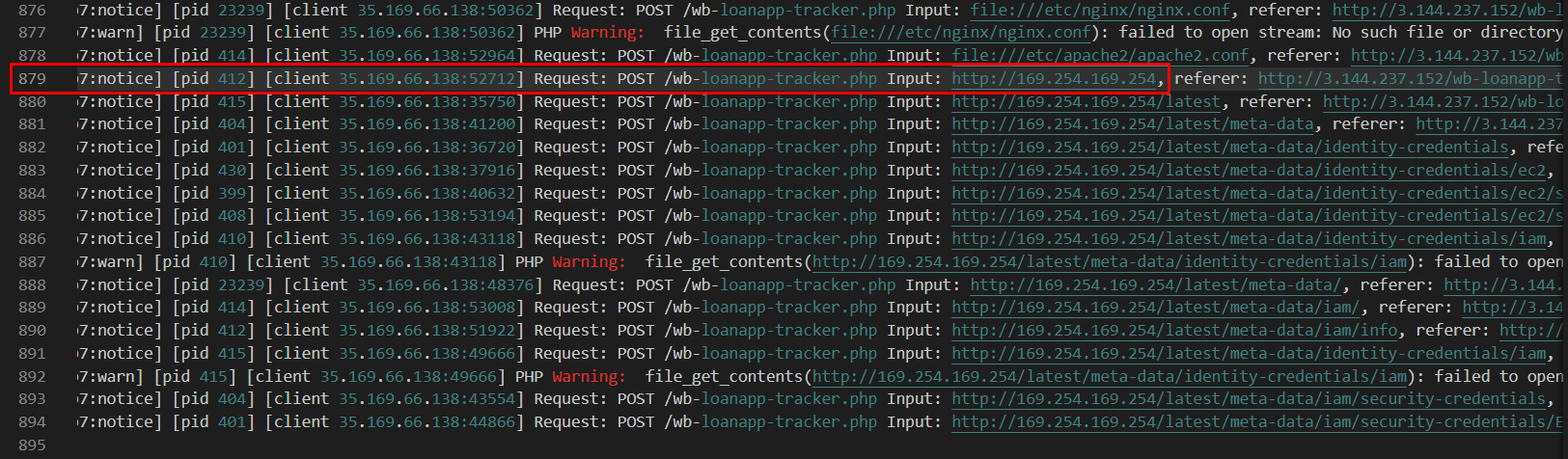
We can see that from here, The Threat actor gained access to cloud metadata of the web server instance.
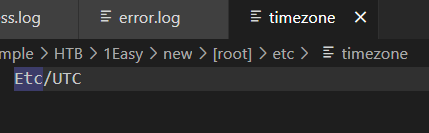
We can confirm /etc/timezone to check the timezone before submit the timestamp and fortunately, this machine is using UTC so we do not need to convert anything.
2024-03-13 14:06:21
Task 6: For a clearer insight into the Database content that could have been exposed, could you provide the name of at least one of its possible tables?
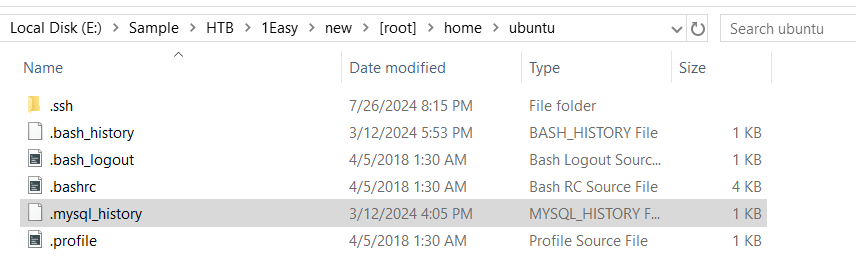
There is .mysql_history file on ubuntu user home directory which stores all sql queries used in mysql on that system
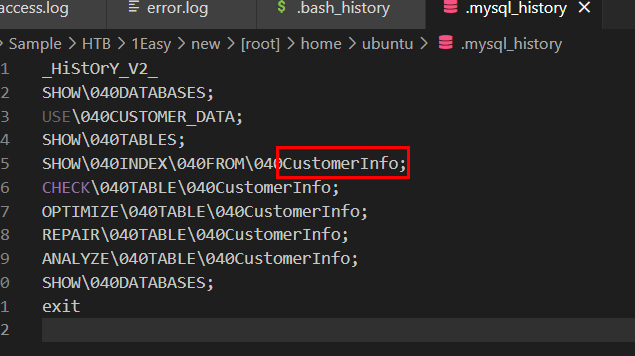
We can see that there is a table name CustomerInfo in CUSTOMER_DATA database so this table is the one that could have been exposed to the threat actor.
CustomerInfo
Task 7: Which AWS API call functions similarly to the 'whoami' command in Windows or Linux?
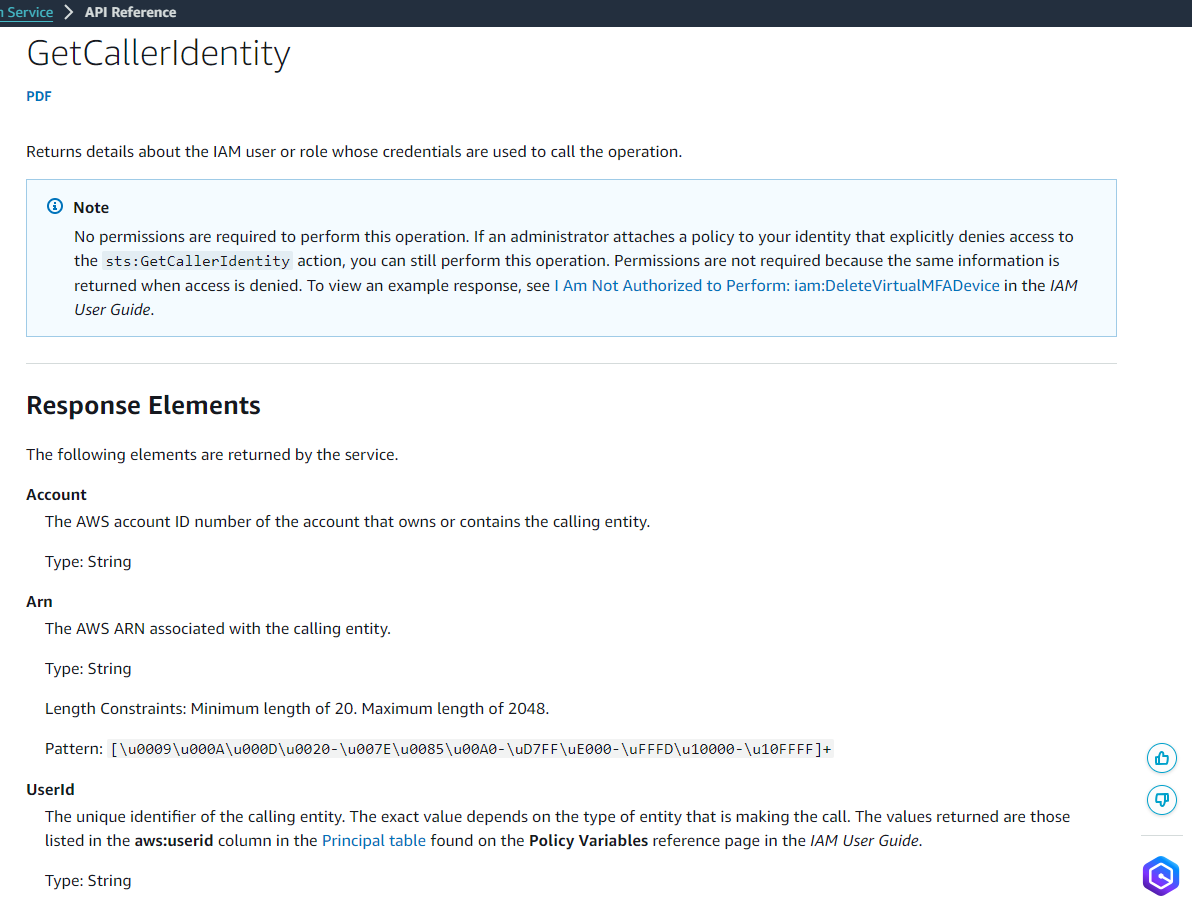
an API call function similarly to whoami command is GetCallerIdentity
GetCallerIdentity
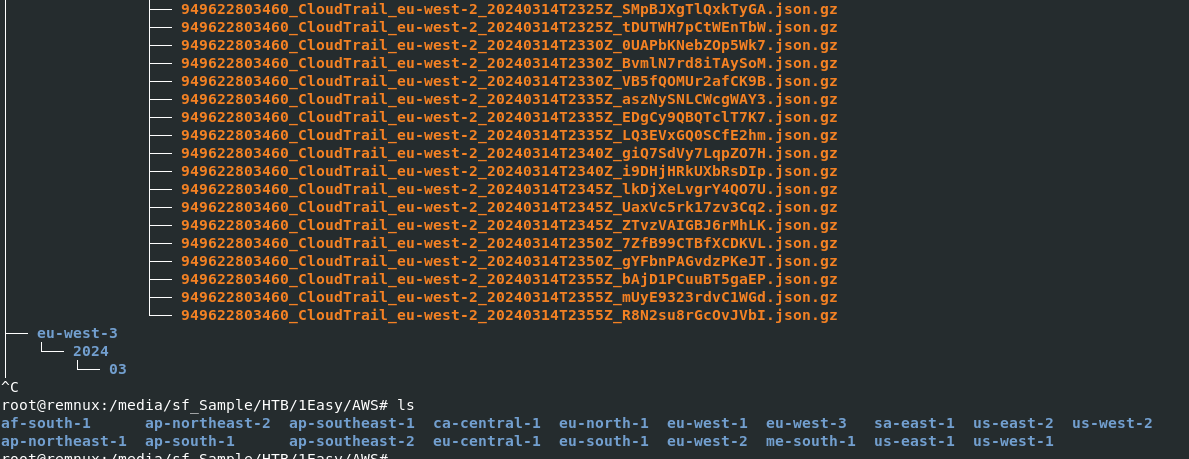
Its time to aggregrate CloudTrail logs to our Splunk instance so we can continue with the rest of this investigation, as you can see that all log files are compressed with gzip
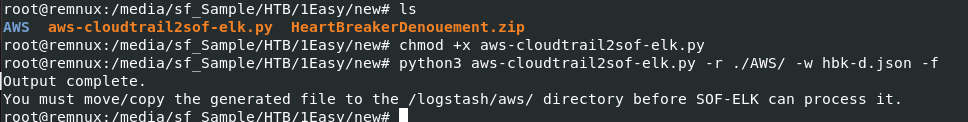
We do not need to use gunzip to decompress them since aws-cloudtrail2sof-elf.py can parse gzip files so lets do it with python3 aws-cloudtrail2sof-elk.py -r ./AWS/ -w hbk-d.json -f and now we should have a single file to import on our Splunk instance.
Task 8: It seems that the reported compromised AWS IAM credential has been exploited by the Threat Actor. Can you identify the regions where these credentials were used successfully? Separate regions by comma and in ascending order.
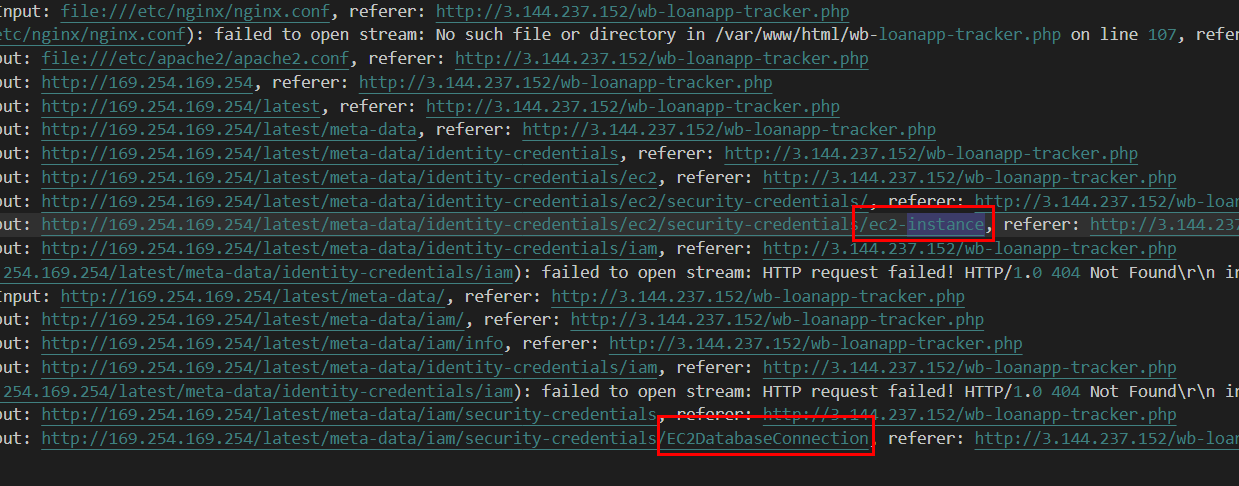
We know that the threat actor had accessed to cloud metadata of web server instance and from this log file, we can see that 2 credentials were compromised
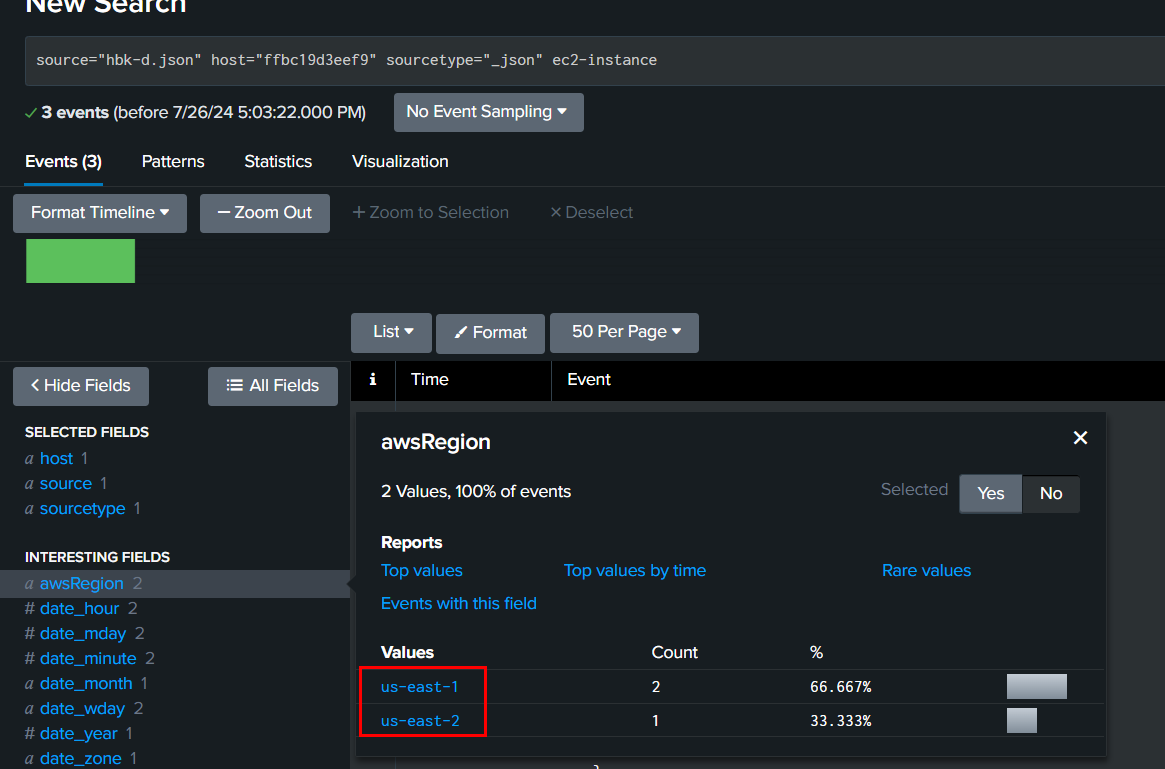
We could not use EC2DatabaseConnection to solve this task since this identity could access all 17 regions but luckily for us that ec2-instance were not widely used and only used on these 2 regions which are correct answers on this task.
us-east-1,us-east-2
Task 9: Discovering that the compromised IAM account was used prior to the web server attack, this suggests the threat actor might have obtained the public IP addresses of running instances. Could you specify the API call the could have exposed this information?
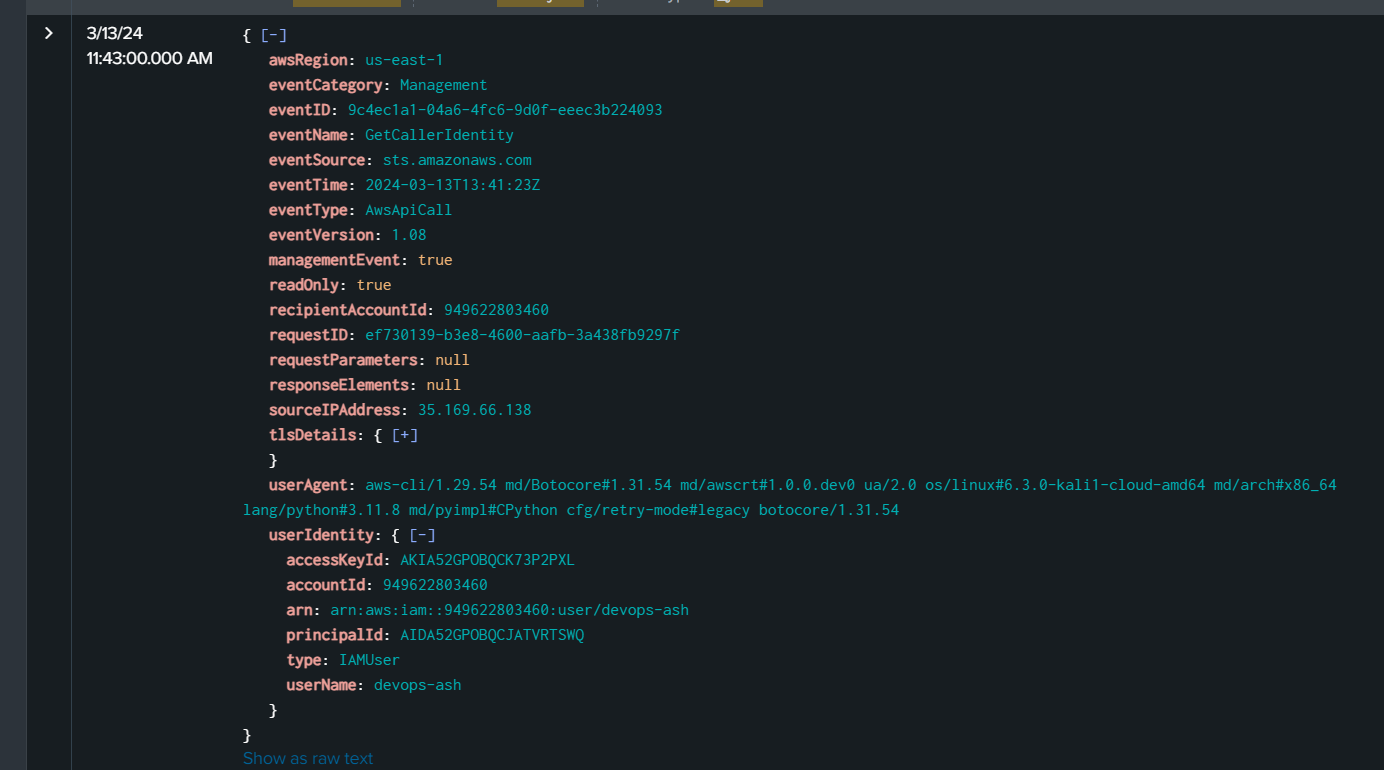
We can suspect that the threat actor used GetCallerIdentity From task 7 and we already know which regions we need to search so lets get userName, arn that the threat actor could get a hand on and sourceIPAddress of the threat actor.
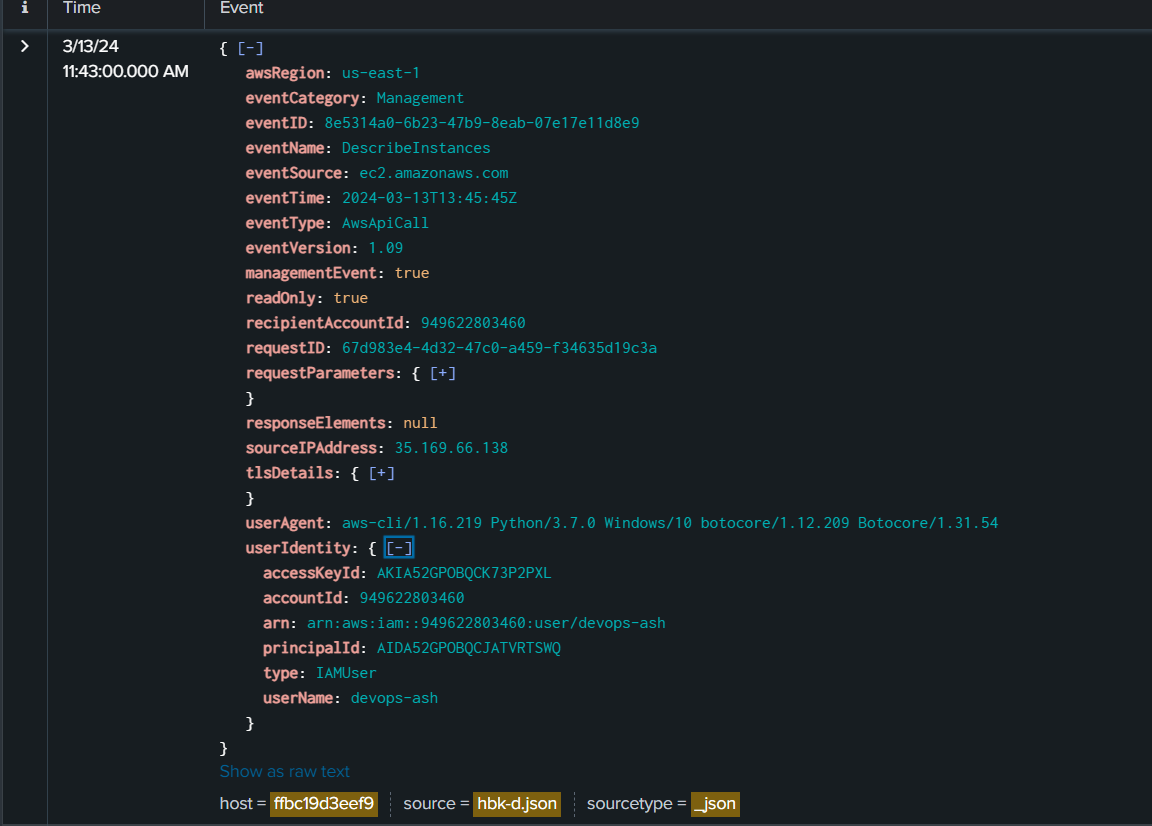
Then we can find any API calls that could expose an information about running instance which there is one particular API call that could do this job which is DescribeInstances
DescribeInstances
Task 10: Looks like the Threat Actor didn’t only use a single IP address. What is the total number of unsuccessful requests made by the Threat Actor?
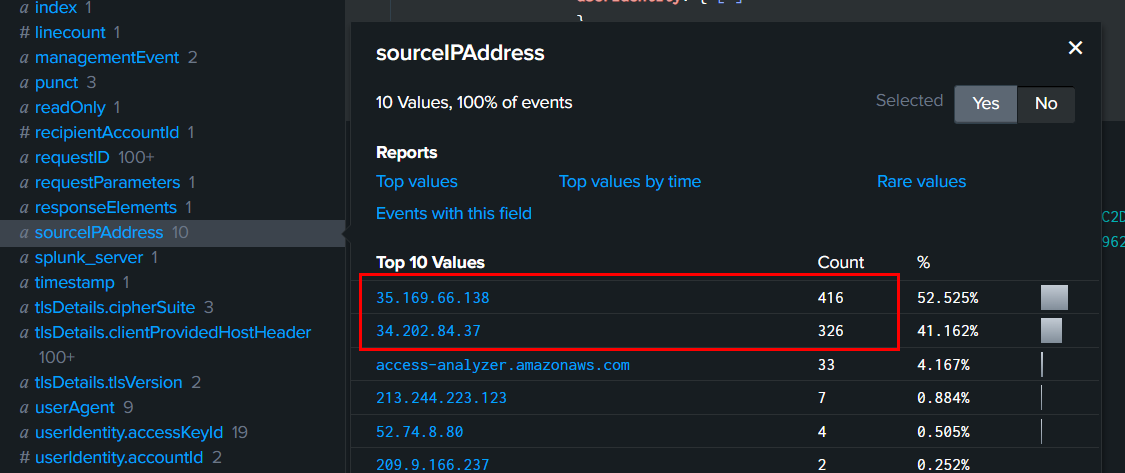
We already know the first IP address of the Threat Actor which is 35.169.66.138 but we need to find another one and one way to find out is to use errorCode="*" and find top 2 sourceIPAddress that appeared with this query, now we have both IP address of the threat actor so we can combine them and answer this task.
742
Task 11: Can you identify the Amazon Resource Names (ARNs) associated with successful API calls that might have revealed details about the victim's cloud infrastructure? Separate ARNs by comma and in ascending order.
There are so many events that could have done this job so I asked ChatGPT to combine all of them to a single search query for me and here is the result that prompt
(eventName="DescribeInstances" OR eventName="DescribeSecurityGroups" OR eventName="DescribeSubnets" OR eventName="DescribeVpcs" OR eventName="DescribeVolumes" OR eventName="DescribeAddresses" OR eventName="GetAccountSummary" OR eventName="ListUsers" OR eventName="ListRoles" OR eventName="ListGroups" OR eventName="GetRole" OR eventName="ListBuckets" OR eventName="GetBucketPolicy" OR eventName="GetBucketAcl" OR eventName="DescribeDBInstances" OR eventName="DescribeDBClusters" OR eventName="DescribeTrails" OR eventName="GetTrailStatus" OR eventName="DescribeStacks" OR eventName="ListFunctions" OR eventName="GetFunction")
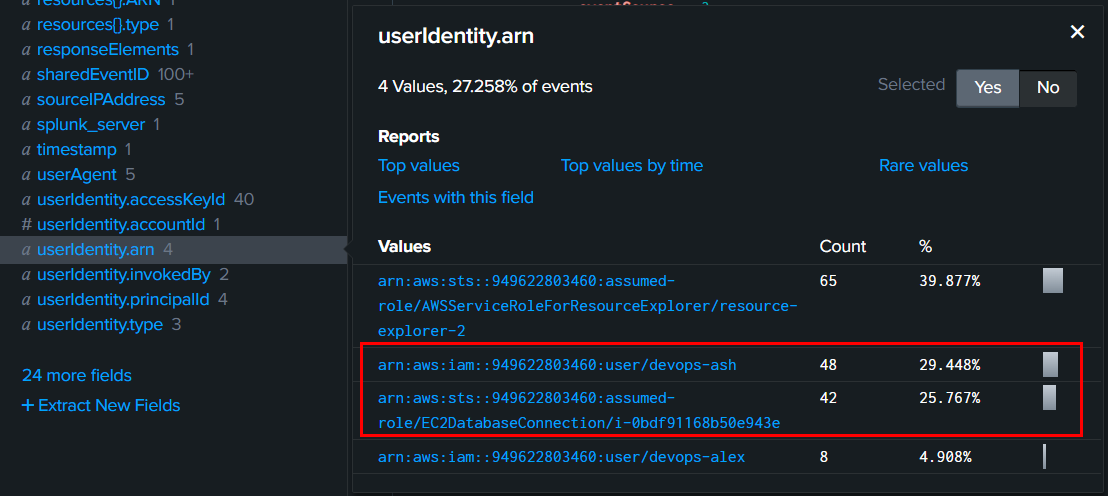
Then go to userIdentity.arn field to separate each arn associated with both threat actor IP addresses
And as we already know that arn:aws:iam::949622803460:user/devops-ash was used by 35.169.66.138 and EC2DatabaseConnection is one of an identity the threat actor got his hand on using SSRF vulnerability
Then after digging a little bit more, we can also confirm that arn:aws:sts::949622803460:assumed-role/EC2DatabaseConnection/i-0bdf91168b50e943e was used by 34.202.84.37 which is another IP address of the threat actor
arn:aws:iam::949622803460:user/devops-ash,arn:aws:sts::949622803460:assumed-role/EC2DatabaseConnection/i-0bdf91168b50e943e
Task 12: Evidence suggests another database was targeted. Identify all snapshot names created. Separate names by comma and in ascending order.
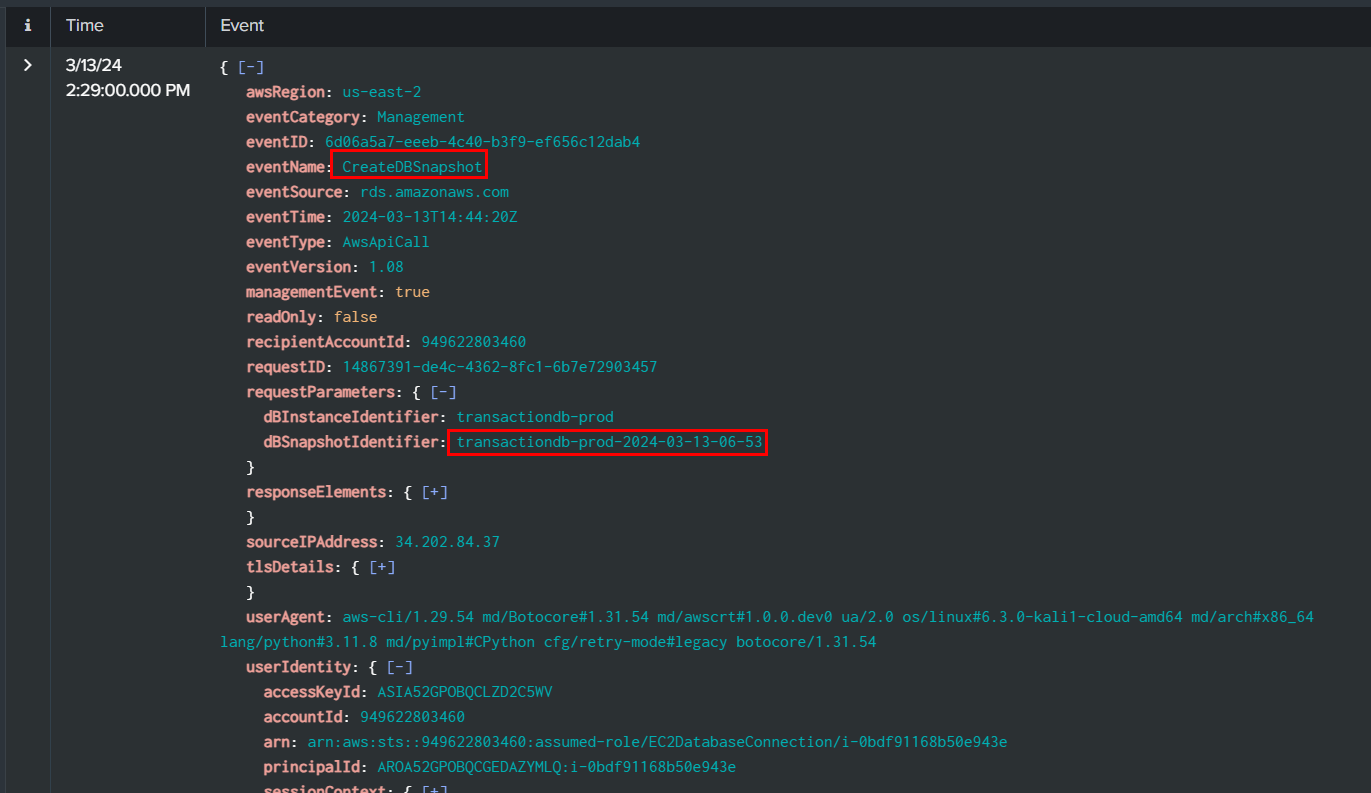
We will have to search for CreateDBSnapshot api call and get dBSnapshotIdentifier of all snapshots created by the threat actor, this is the first one
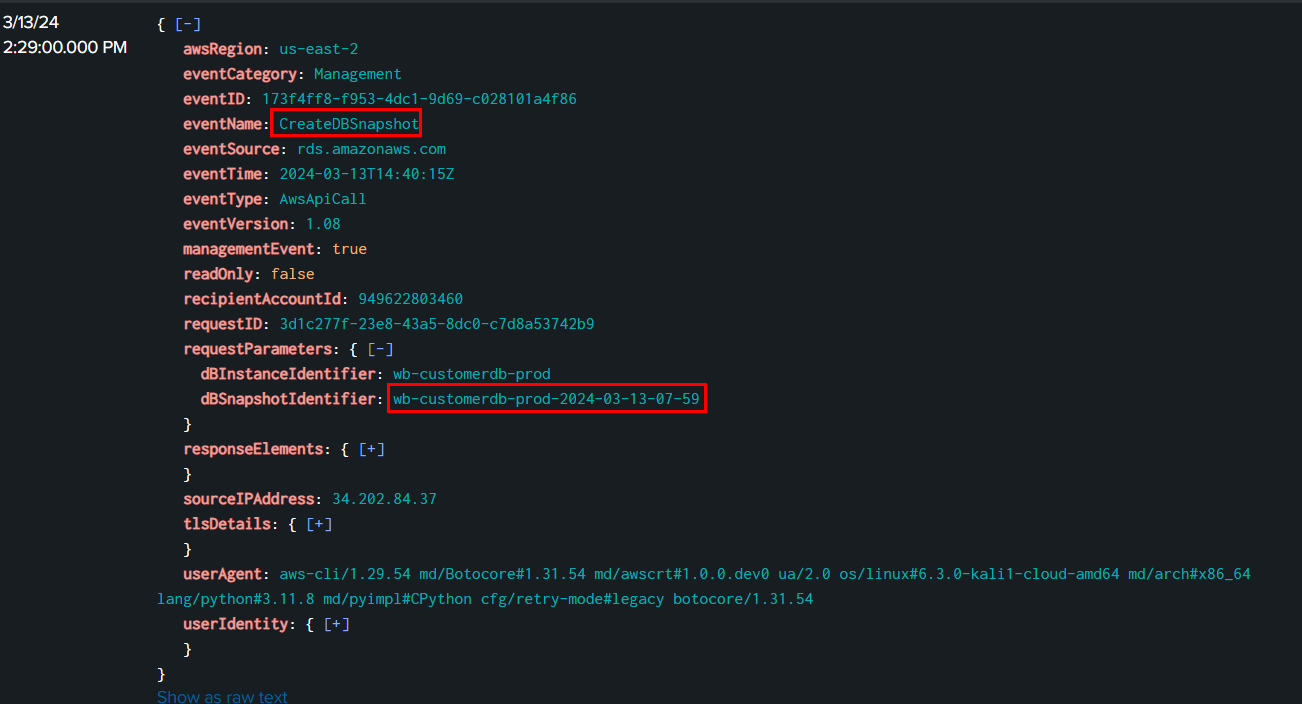
And this is the second one, the threat actor only created 2 DB snapshots so we can submit both as an answer of this task rightaway.
transactiondb-prod-2024-03-13-06-53,wb-customerdb-prod-2024-03-13-07-59
Task 13: The Threat Actor successfully exfiltrated the data to their account. Could you specify the account ID that was used?
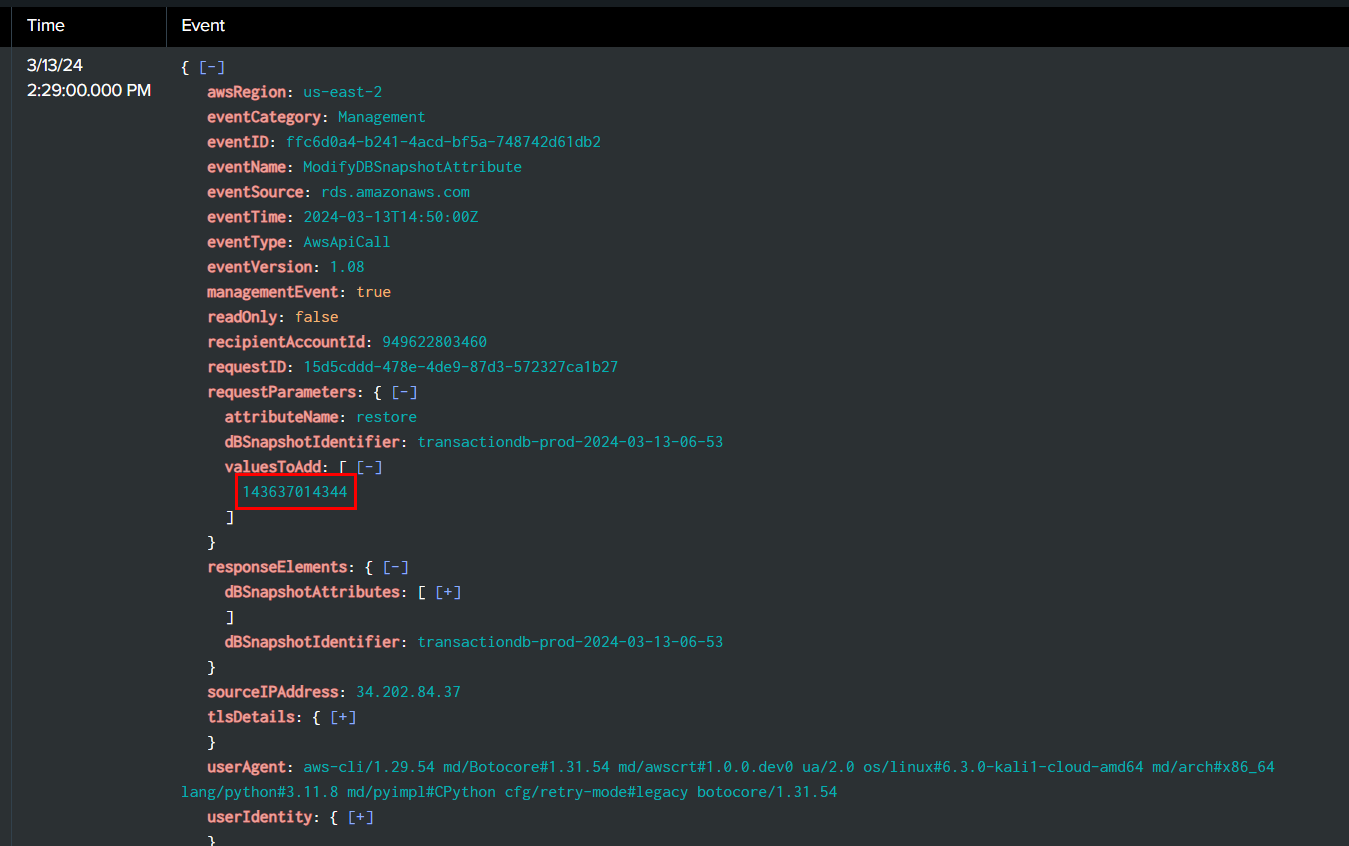
We can search for one of dBSnapshotIdentifier, we found earlier and obtain the value of valuesToAdd field
When I gave a hint to my new friend on discord, he gave me this link which is related to this technique directly (RDS snapshot exfiltration) so if possible, you should give it a try!
143637014344
Task 14: Which MITRE Technique ID corresponds to the activity described in Question 13?
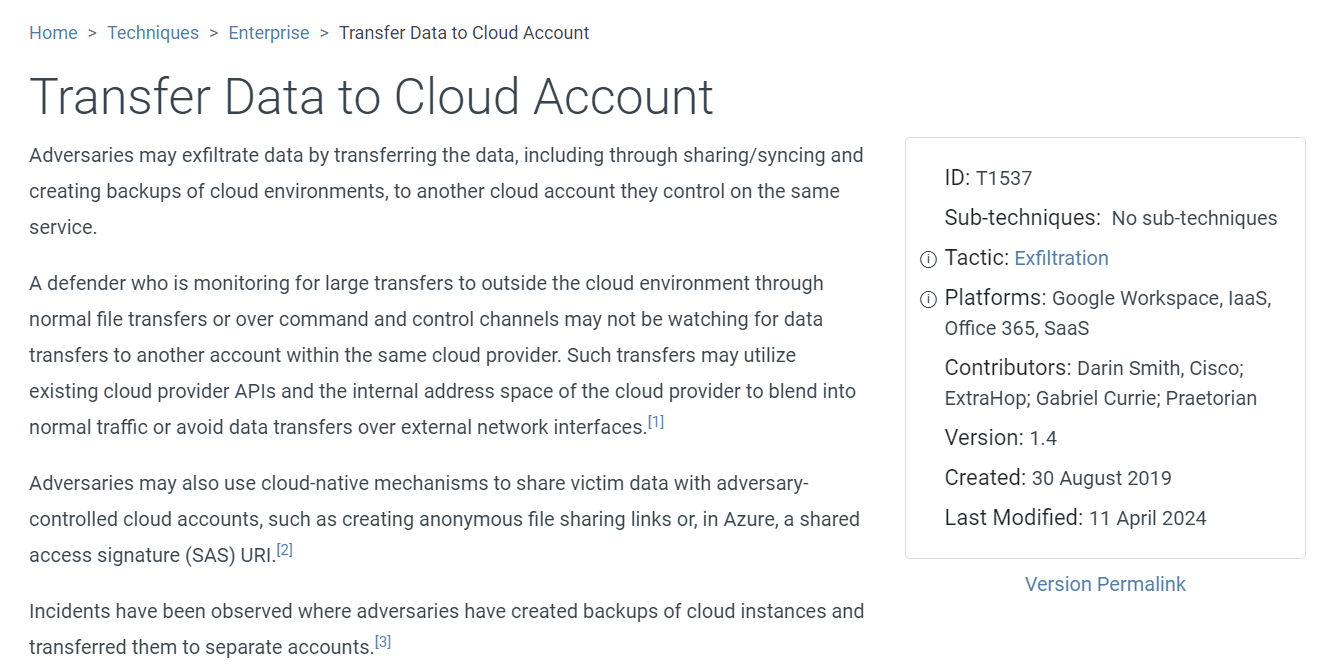
This technique is called Transfer Data to Cloud Account according to MITRE ATT&CK framework.
T1537
 https://labs.hackthebox.com/achievement/sherlock/1438364/700
https://labs.hackthebox.com/achievement/sherlock/1438364/700
 Scenario:
Your digital forensics expertise is critical to determine whether data exfiltration has occurred from the customer’s environment. Initial findings include a compromised AWS credential, indicating a potential unauthorized access. This investigation follows from a customer report of leaked data allegedly for sale on the darknet market. By examining the compromised server and analyzing the provided AWS logs, it will not only validate the customer's breach report but also provide valuable insights into the attacker's tactics, enabling a more comprehensive response.
Scenario:
Your digital forensics expertise is critical to determine whether data exfiltration has occurred from the customer’s environment. Initial findings include a compromised AWS credential, indicating a potential unauthorized access. This investigation follows from a customer report of leaked data allegedly for sale on the darknet market. By examining the compromised server and analyzing the provided AWS logs, it will not only validate the customer's breach report but also provide valuable insights into the attacker's tactics, enabling a more comprehensive response.






















 https://labs.hackthebox.com/achievement/sherlock/1438364/700
https://labs.hackthebox.com/achievement/sherlock/1438364/700